Texas Tech Health Sciences Centers (HSCs) in Lubbock and El Paso must inform more than 1.4 million people their personal information was compromised in mid-September cyber-attack, LubbockLights.com has confirmed. In some cases, that might include private information about diagnosis and treatment.
Related story: UMC paid ransom with insurance, data was restored, not sold on dark web
The HSCs were required to report the breach within 60 days to the U.S. Department of Health and Human Services Office for Civil Rights, which then publicly disclosed 650,000 people of Lubbock’s HSC were affected. Add 815,000 in El Paso. Lubbock and El Paso are separate universities under the Texas Tech University System.
A relatively new ransomware organization called Interlock claimed responsibility, now offering the private data – 3.2 terabytes – for download, according to several technology websites.
The HSCs did not confirm claims by Interlock.
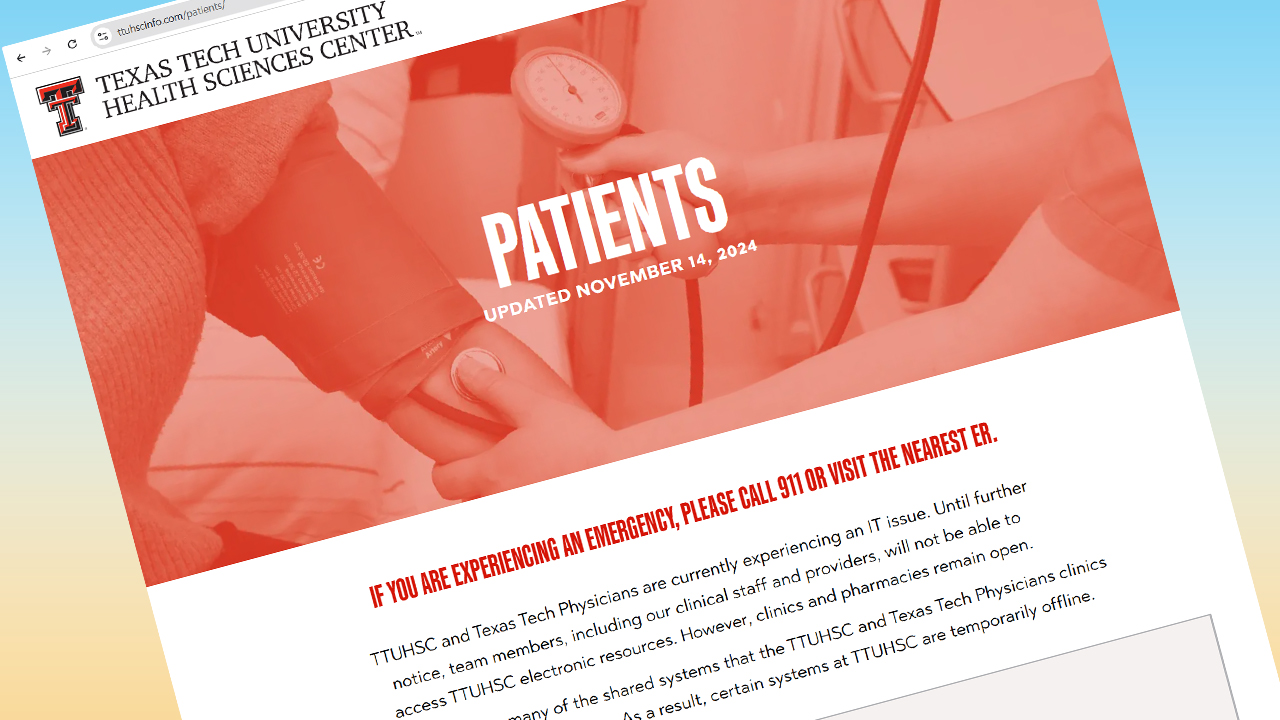
“At this time, the HSCs will not be making further comments until the investigation is complete,” it said, referring LubbockLights.com to a November 25 statement.
That statement – on both HSC websites – said, “The information varies by each individual, but may include name, date of birth, address, Social Security number, driver’s license number, government-issued identification number, financial account information, health insurance information and medical information, including medical records numbers, billing/claims data and diagnosis and treatment information.”
The breach happened at the same time University Medical Center was compromised. UMC was able to get its systems back up and running. The HSCs announced their patient portals are mostly back up and running as of October 31. But there were still computer issues as of November 14.
LubbockLights.com searched the Internet and, by contrast, did not find claims that UMC’s patient data was available for download.
In the meantime, LubbockLights.com asked Lubbock’s HSC to ask:
- Was a ransom demanded? If so, how much?
- Did the HSCs indicate a willingness to pay?
- Do the schools have insurance policies covering ransomware or cyber security events?
- How much will it cost to inform patients?
- Are the schools back up and running normally?
- Can you confirm public statements that Interlock is responsible for the attack?
So far, the questions remain unanswered.
What is Interlock?
According to the HIPAA Journal, Interlock is a new ransomware group conducting attacks since at least September.
“Interlock ransomware is a financially motivated threat group that claims that in addition to conducting attacks for monetary gain …” said an article written by Steve Alder, editor-in-chief of The HIPAA Journal, adding Interlock also claims it wants to teach lessons to large organizations for poor security practices.
“Interlock engages in big-game hunting, targeting large organizations with the financial means to pay large ransoms,” Alder reported.
More than one online source quoted Interlock as saying, “We are Interlock, a relentless collective that exposes the recklessness of companies failing to protect their most critical assets: customer data and intellectual property. We exploit the vulnerabilities they leave wide open, delivering a harsh but necessary wake-up call to those who think they can cut corners on security.”
“We don’t just want payment; we want accountability,” the group claimed.
The group gains initial access to a victim’s network by tricking a user into installing a fake Google Chrome browser update, reported Alder.
Why are they hard to stop?
There are many reasons these cybercriminals are hard to catch, according to a number of articles.
- There are too many ransomware attackers spread around the world. The incentives are strong to keep up the attacks. International investigations often require extensive diplomatic cooperation among multiple nations and agencies.
- Ransomware is here to stay for years to come because there are plenty of security-poor organizations and poorly regulated payment systems like cryptocurrency.
- Attacks can originate from anywhere in the world. Cybercriminals can operate from countries with weak regulations, and use masking techniques a to hide their real location.
More about an Interlock attack
Technology company Cisco offers the “Cisco Talos Incident Response” (CTIR) as one of its services.
CTIR said of Interlock, “The group has notably targeted businesses in a wide range of sectors, which at the time of reporting includes healthcare, technology, government in the U.S. and manufacturing in Europe, according to the data leak site disclosure, indicating their targeting is opportunistic.”
Interlock gets foothold on the victims’ computer systems about 17 days before deploying its ransomware, CTIR also said.
Once the computer system is compromised, a ransom note is displayed on the various users’ login screens.
“In the ransom note, the attacker warns against attempting to recover the encrypted files,” CTIR stated online.
The attackers also demand a response within 96 hours or else they threaten to release the private information and notify the media.
Please click here to support Lubbock Lights.
Comment, react or share on our Facebook post.
 Facebook
Facebook